The Los Angeles County District Attorney’s Office issued an alert in November warning travelers to avoid using USB charging stations in hotels, airports and train stations “because they may contain dangerous malware.”
The USB charger scam has been dubbed “juice jacking.”
Hackers tamper with charging cables and attach them to public USB outlets. When travelers plug their phones or laptops into these hacked cables, cyber-criminals can access the traveler’s device, steal credit card data and passwords or even demand ransomware.
“Attackers are always innovative. They’re one step ahead of everyone,” says Iftah Bratspiess, CEO of Israeli startup Sepio Systems, “rogue devices” including manipulated cables.
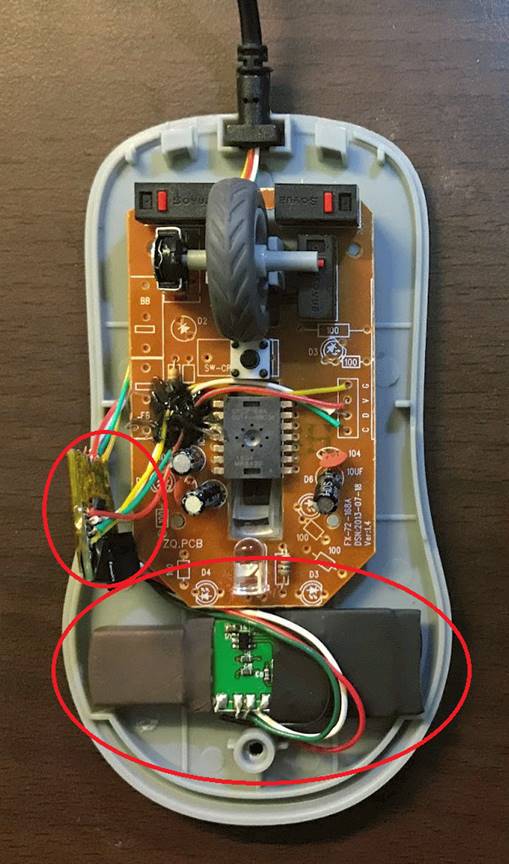
Bratspiess tells ISRAEL21c that hackers know people don’t willingly plug an unfamiliar storage device into their machine, but they think of charging cables and power banks as batteries, not IT devices. “They see an open USB port in a conference room or a café and will use it without thinking twice.”
A doctored cable can easily be implanted with a Bluetooth or Wi-Fi remote control. Once it’s connected to your phone or laptop (or worse, an entire network server), software hidden in the cable “impersonates” a mouse or a keyboard, and thus capture keystrokes, mouse moves and data.
“It can open a browser and go to a URL where malware is waiting to be downloaded and that’s it,” Bratspiess warns.
Anyone can go online and buy a USB Ninja Cable, ostensibly “an information security and penetration testing tool” for police and government, but attractive to hackers because it is “undetectable by firewalls, AV software or visual inspection,” according to the manufacturer.
Another dubious website, Hak5, is chock-a-block with devices ready for hacking, including an implant intended for installation on-site that displays a seemingly hand-written label: “IT do not remove.” There’s also a USB “rubber ducky” as seen on the TV show “Mr. Robot.”
Detects rogue devices
Sepio System’s Sepio Pro is intended mainly for large enterprises in finance, insurance and telecommunications.
The software is designed to detect any rogue device, even if it was previously authorized. That’s important since hackers can set their cable-delivered malware to “sleep” for a certain time, so as not to set off early alarm bells.
Sepio Pro gives corporate IT managers an easy-to-follow visual interface that identifies vulnerabilities by icons and color.

“Once we’ve detected a rogue device, we’ll notify the other security systems in the company,” Bratspiess says.
The IT department can then decide whether to remove or block the rogue device immediately or wait for the next hardware refresh cycle.
“In some cases, it’s better to let it be, to see who comes to pick it up or change it,” Bratspiess says. “If you block it, then the attacker knows.”
Hardware attacks are growing
What types of devices should you be wary of? Innocent-appearing gadgets like a standard Ethernet connector or a USB cup warmer. In the latter, “you place your coffee cup on it and the USB power keeps the cup warm. It’s often given away as a gift,” Bratspiess points out.
So are USB cables: “If a hacking group is targeting a certain enterprise and they know employees drink coffee at a nearby Starbucks, they can send someone over there to give away free charging cables,” Bratspiess adds. Or it could be at a trade show or a promo day at a startup – the possibilities for crafty hackers are seemingly endless.
USB charging cables may be the easiest devices to hack, but some other high-profile hardware attacks made the news last year.
Bloomberg reported that China had installed spy chips on motherboards installed by US-headquartered Supermicro. (The company’s motherboards are used by tech companies like Apple and Amazon in their servers.)
And earlier this summer it was revealed that NASA had been hacked in 2018 when an unauthorized Raspberry Pi device was attached in the organization’s Jet Propulsion Laboratory. Communication with satellites has yet to be fully restored “because of continuing concerns about [data] reliability,” NASA confirmed.
All of this is keeping Sepio busy. The company has 25 customers in the United States, Singapore, Brazil, South Africa and Israel, including partnerships with IT integration providers Tech Data, SHI International and Tyco Integrated Security (now a part of Johnson Controls).
Bratspiess and his cofounders, CMO Bentsi Ben-Atar and CEO of Sepio Systems’ North America office Yossi Appleboum, have been working together for more than 25 years, since they were together in the IDF’s 8200 intelligence unit. In 2013, the trio’s company WebSilicon was acquired by security integration leader Magal. Sepio was founded in 2016.
Sepio (the name means “secure” or “guard” in Latin) has raised $6.5 million. The first round included funding from electric utility Energias de Portugal, which is also a customer.
Sepio won Frost & Sullivan’s 2019 European Enabling Technology Leadership award for the Rogue Device Mitigation market.
As for the problem of how to stay safe while charging in public, the best advice is to bring your own charger, use an AC power outlet, or buy a “USB condom” that shields your device from the data pins on USB chargers.
If you’re not a high-profile target, a hacker “might scan your WhatsApp messages or pictures, but they’ll move on,” Bratspiess says. “But if you have something to hide, use the condom!”
For more information, click here.